What is a phishing e-mail and how can you recognise it?
No doubt you have already received an e-mail in which a company or a bank asks you to pay an outstanding invoice of which you are completely unaware. This is a classic example of a phishing attempt. And the (fake) company or bank uses this technique to get hold of your money or personal details. Falling prey to phishing scams can have serious financial consequences and compromise your cybersecurity. That is why we have compiled a list of the main tips you should know to recognise phishing attempts in time.
What is phishing? How does it work?
Phishing is a scam where somebody tries to steal certain information from you over the Internet.
The attacker pretends to be a trustworthy entity, sometimes even someone you know, attempting to gain your trust. Therefore, the fake e-mail he sends you looks authentic; usually it even includes the logo of the real company he pretends to work for (your bank, a web store where you regularly shop…).
In such a fake e-mail, the phisher will often tell you that you need to log in to settle an outstanding balance or to win a prize. In order to do this, he will ask you to click on a link, which will lead you to a fake website. There, the phisher will ask you to enter your details or make a payment. And that is how a phisher will get hold of your details or money without you even noticing!
The term 'phishing' was first used in 1996, when hackers tried to steal passwords from America Online (now AOL) users. They compared this technique to that used in fishing, as they used their fake e-mails to cast lines into the 'sea' of Internet users. And just like when fishing for fish, it only takes a few people to take the bait for a phishing attack to be successful.
Basically, cybercriminals increasingly make use of phishing techniques because it is much easier to get people to click on a link than breaking into their computers.
Important:
Incidentally, cybercriminals misuse virtually any means of telecommunication to launch their attacks (telephone, text message, social media, e-mail…). In this article, we will focus on e-mail, which is the most common method, but be wary of other means of telecommunication as well!
How do I recognise a phishing e-mail?
Unfortunately, phishing e-mails are increasingly harder to spot. Often, they are exact duplicates of the e-mails you receive from legitimate companies, including the logo and all. And whereas previously you could effortlessly spot phishing e-mails just by looking at the poor English, it has now become quite a difficult task because of the improved language. But although it is difficult to recognise phishing attempts, you cannot miss them if you follow the five tips below that will help you recognise and prevent them.
- Make sure to check the e-mail address of the sender, and not just the name. In many cases, the domain name will not match the official domain name of the counterfeit organisation.
- Check if the content of the e-mail is spelled correctly. Cybercriminals are often bad at spelling. As mentioned above, phishing e-mails are often written a bit better, but the slightest mistake should be enough to make you realise that you are dealing with a suspicious e-mail.
- Do not click on unknown links. Instead, when opening an e-mail on a computer, hover your cursor over the link. This way, the link will show the destination URL. If this URL looks strange or does not match the actual website of the organisation that supposedly sent the e-mail, it is better not to click on it.
- Do not download images or files contained in suspicious e-mails.
- You should never enter your username or password on a website without making sure it is an official page!
The sender: often a first sign of phishing
Cybercriminals use different techniques to fool you. In the first place, they use a fake sender address. This technique, called ‘spoofing’, is super simple. Anyone can indeed enter a fake sender name in an e-mail client.
There is no infallible way to find out who the real sender of an e-mail is. However, the route the e-mail took to arrive can provide you with an indication of the sender. You can find this route by having your e-mail client show all headers (please see our instructions for Thunderbird, Outlook, MacMail…).
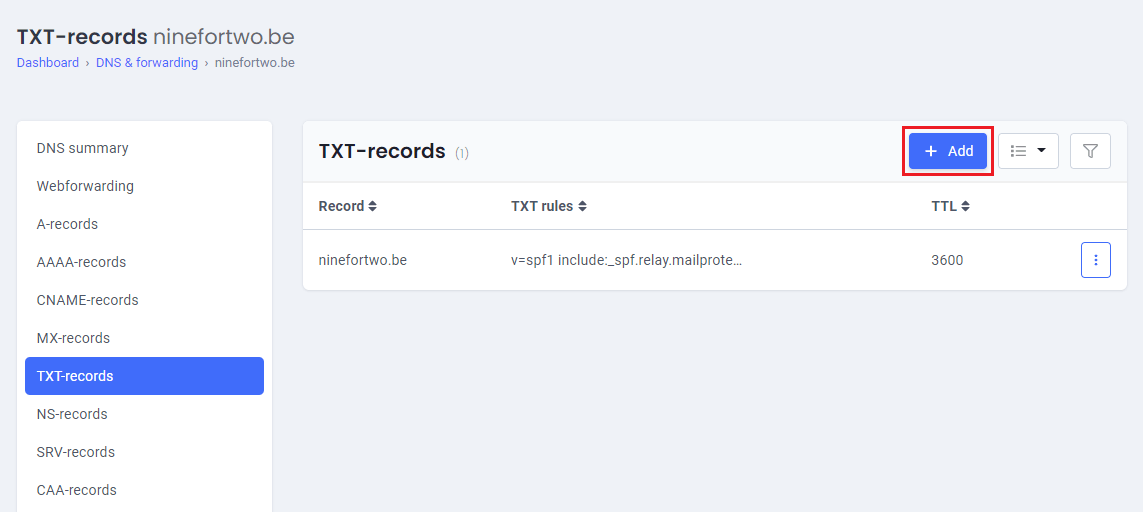
You can also help by making sure that others cannot spoof your e-mail address. For this, you need to create an SPF record on your domain (please see: creating an SPF record).
Even if you are protected against spoofing, it is always better to check the sender. Not every phisher uses spoofing techniques, so be sure to remove messages with a suspicious sender first.
The link in the e-mail gives away a lot of information
Usually, the link included in a phishing e-mail is also perfectly hidden. Behind a seemingly harmless ‘click here’ button, the attacker can easily include the address of his bogus website. And even if a URL in mentioned in the text, the web address behind the link can be totally different. Even if the text says www.mycompany.be, for example, the link can still point to another address.
- If you are working on your desktop computer, activate your status bar (View>Status Bar) in your e-mail client or web browser. Hover your cursor over the link, and you will now see the address in the status bar. Or right click on the link and copy/paste from your clipboard so that you can examine it.
- If you are checking your e-mail on your iPad or iPhone, long tap the link. A pop-up menu will reveal the real address.
- Analyse and try to understand the link structure. The real web address to which you are redirected consists of the domain name plus an extension (.be, .com, .biz, .shop…), which are located right before the first slash (/). So, do not be fooled by an address such as ‘https://postbank.be.fraud.com/login’, where fraud.com is the actual (fraudulent) web address, not postbank.be!
- Also, be careful with ‘homographic spoofing’, a technique whereby certain letters in a domain name are replaced by visually indistinguishable characters. The letter O, for instance, may be replaced by a 0 (zero), an i by a !, an I (capital i) by an l (small l) . Wikipedia will provide you with further information on homograph attacks.
- Be very careful with URL shorteners such as t.co or goo.gl. Just assume that there is no legitimate reason for shortening a URL in an e-mail!
- And, last but not least: in case of doubt, you should enter the address of your bank, web store, etc. yourself.
What is the purpose of a phishing e-mail?
The attacker’s intention is to steal your confidential information (login, password, bank details…) or infect your computer with malware (spyware, keylogger, ransomware…).

The e-mail may contain an attachment that you will open without a second thought. Or it may include a link, which redirects you to the fraudulent website of the company, where you will enter your login details without any suspicion.
If you enter your personal details on such a fake website or control panel, the cybercriminal will be able to use them to access your online banking accounts, make purchases, etc. Your identity can also be used to commit fraudulent acts or scams, whereby the cybercriminal pretends to be you. In the case of the Combell phishing e-mail, the attacker would have been able to use your login details to log in to the My Combell control panel and access databases containing information about your users.
Why are you the target of a phishing e-mail?
The fact that you received a phishing mail does not mean the attacker got hold of your personal details by hacking the company of which he is misusing the name.
Attackers use all sorts of tricks to get hold of e-mail addresses of potential victims. Consider, for example, the publicly available Whois details related to domain names, the names and contact details of collaborators that are included on a company’s website, social media, etc. The Internet provides an astounding amount of personal information about many people, which is a real shame according to an increasing number of users!
The fact that you received a phishing mail does not mean the attacker got hold of your personal details by hacking the company of which he is misusing the name.
A company like Combell can thus also be at the centre of a phishing scam. In the past, alert customers have already reported cases of fake e-mails that invited them to log in to a very convincing imitation of the My Combell login panel. And those who logged in to it unknowingly provided their login details (username and password) to a cybercriminal.
And yet, Combell was not hacked: all the cybercriminal had to do to contact customers was to look up the Whois information that is publicly available for every domain name. This means he did not need to access our data – which are, incidentally, optimally protected.
Of course, we always take immediate action in cases of phishing scams in order to stop any phishing attempts. If we become the target of any future phishing attacks, you will certainly read about it on our blog, on our Facebook page or on Twitter.
However, e-mails are often sent to randomly generated addresses. You most probably already received a phishing e-mail from bank XYZ, with which you do not even have an account… However, we strongly recommend that you report any phishing attempt to the company whose name has been misused, and to SafeOnWeb.
It is, of course, possible that some personal information comes from companies that have been hacked. You can check for yourself whether your personal details were ever accessed in a data breach by visiting the website 'Have I Been Pwned'?


